Automated security testing for infrastructure as code in DevSecOps pipelines.
Client
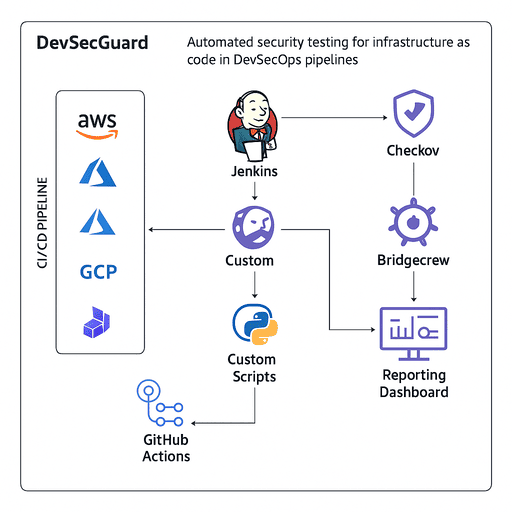
DevSecGuard is a DevSecOps solution designed to automate security testing for infrastructure as code (IaC) within CI/CD pipelines, developed for a large-scale technology firm. The project aimed to embed security practices early in the development process, minimizing risks from misconfigured infrastructure.
Project Objectives: The primary goal was to reduce the number of misconfigurations in IaC templates and ensure compliance with security best practices, such as CIS benchmarks and NIST 800-53. The client required a scalable solution to handle thousands of deployments across multiple cloud environments, including AWS, Azure, and GCP.
Implementation Process: I initiated the project by integrating Checkov, an open-source IaC scanning tool, into the existing CI/CD pipeline managed by Jenkins. This allowed for automated scanning of Terraform and CloudFormation templates to detect misconfigurations and vulnerabilities. I also developed custom validation scripts using Python to enforce organization-specific security policies, such as restricting public S3 buckets and enforcing encryption. To streamline the process, I configured GitHub Actions to trigger security scans on every code commit, providing immediate feedback to developers.
Security Enhancements: To further secure the pipeline, I integrated Bridgecrew for continuous IaC posture management and OPA (Open Policy Agent) to enforce runtime security policies. I also implemented a reporting dashboard using ELK Stack (Elasticsearch, Logstash, Kibana) to visualize scan results and track compliance trends, enabling the team to address issues proactively.
Results and Impact: DevSecGuard achieved a 50% reduction in IaC misconfigurations , improved compliance with security standards by 85% , and reduced the mean time to detect (MTTD) and resolve (MTTR) security issues by 40% . These improvements enhanced the overall security posture and accelerated the deployment cycle for the client.
Technologies Used: Terraform and CloudFormation for IaC, Checkov and Bridgecrew for scanning, OPA for policy enforcement, Jenkins and GitHub Actions for CI/CD, Python for scripting, and ELK Stack for monitoring and reporting.
Challenges and Lessons Learned: A key challenge was balancing the speed of development with the thoroughness of security scans, as excessive checks could slow down the pipeline. This required optimizing scan configurations and prioritizing critical vulnerabilities, teaching me the importance of performance tuning in DevSecOps. The project also underscored the need for developer training to ensure adoption of security best practices.
Your email address will not be published. Required fields are marked *